Differences between CVE, CWE, and CVSS


In the field of cybersecurity, a variety of specific terms and abbreviations can be easily confused due to their similarity. Notably, CVE, CWE, and CVSS are three examples, each representing a different concept.
This article will explore the differences between CVE, CWE, and CVSS to gain a better understanding of their distinct roles and significance.
What Is CVE?
CVE stands for Common Vulnerabilities and Exposures. It is a dictionary of publicly known information security vulnerabilities and exposures. CVE is a standardized way of identifying and naming vulnerabilities in software and hardware. Each vulnerability is assigned a unique identifier, known as a CVE ID (e.g., CVE-2021-44228), which allows security researchers, vendors, and users to reference and track specific vulnerabilities.
The purpose of CVE is to provide a common language for discussing vulnerabilities, making it easier to share and exchange information about them. It enables organizations to identify and prioritize vulnerabilities, ensuring that appropriate measures are taken to mitigate the risks associated with them.
What Is CWE?
CWE stands for Common Weakness Enumeration. It is a community-developed list of software and hardware weaknesses that can lead to vulnerabilities. Unlike CVE, which focuses on specific vulnerabilities, CWE focuses on the underlying weaknesses that can be exploited to create vulnerabilities.
CWE provides a standardized way of describing and categorizing weaknesses, making it easier to understand and address them. Each weakness in the CWE list is assigned a unique identifier, known as a CWE ID (e.g., CWE-20), which helps in identifying and discussing specific weaknesses across different systems and applications.
The main goal of CWE is to improve the quality and security of software by providing a common language for discussing weaknesses. By addressing the underlying weaknesses, developers and security professionals can prevent vulnerabilities from occurring in the first place.
What Is CVSS?
CVSS stands for Common Vulnerability Scoring System. It is a framework for assessing the severity and impact of vulnerabilities. CVSS provides a standardized method for calculating a numerical score, known as the CVSS score, which represents the overall severity of a vulnerability.
The CVSS score takes into account various factors, including the exploitability of the vulnerability, the impact it can have on the affected system, and the level of access required to exploit it. The score ranges from 0 to 10, with 10 being the most severe.
The purpose of CVSS is to help organizations prioritize vulnerabilities and allocate resources accordingly. By assessing the severity of vulnerabilities, organizations can determine which vulnerabilities require immediate attention and which can be addressed at a later stage.
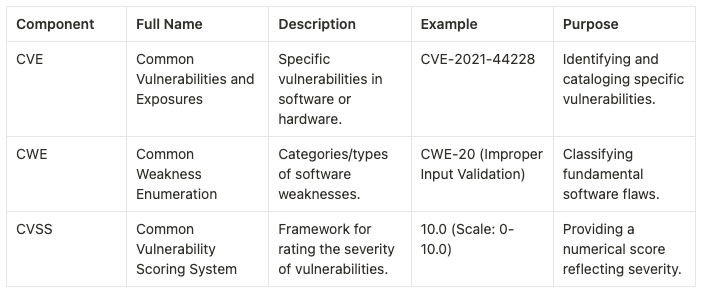
Differences between CVE, CWE, and CVSS
While CVE, CWE, and CVSS are all related to cybersecurity, they serve different purposes and focus on different aspects of vulnerabilities and weaknesses.
CVE is a dictionary of known vulnerabilities and exposures, providing a standardized way of identifying and naming vulnerabilities. It allows for easy referencing and tracking of vulnerabilities.
CWE, on the other hand, focuses on the underlying weaknesses that can lead to vulnerabilities. It provides a common language for discussing weaknesses and helps in addressing them to prevent vulnerabilities.
CVSS, is a scoring system that assesses the severity of vulnerabilities. It provides a numerical score that helps in prioritizing vulnerabilities and allocating resources accordingly.
While CVE and CWE are more focused on the identification and categorization of vulnerabilities and weaknesses, CVSS is focused on assessing their severity and impact.
Overall, CVE, CWE, and CVSS are all valuable parameters that are commonly used in security assessments. They work together to provide a comprehensive approach to vulnerability management, allowing organizations to identify, address, and prioritize vulnerabilities effectively.
By understanding the differences between these terms, organizations can better manage and mitigate cybersecurity risks.